June 2021
Download
Apple iOS 14.6 and macOS Big Sur 11.4 include new audio features and more.
Versions of QuickBooks desktop prior to 2019 will be unable to use payroll after May 31, 2021.
Microsoft’s Exchange Server system (Office 365) sent all inbound mail into Junk Email on Wednesday, May 26 from 12:50 PM to 3:15 PM.
Amazon seized, destroyed two million fake products
Over 10 billion suspect listings were also wiped out during the year in a counterfeit crackdown. Brand Protection Report (.PDF)
A data leak earlier this month implicated approximately 200,000 individuals in a review scam — potentially originating from China — in which sellers ‘refund’ a product’s price once a glowing review is left on the item’s Amazon listing.
Windows 10: Version 1803, 1809 and 1909 has reached end of life May 11, 2021.
These editions no longer receive security updates.
Microsoft adds Consumer Features to Teams
The Teams Chat experience now supports adding people via their email or phone number. And people who don’t have or want to use Teams can participate in Chats over SMS messaging on their smartphones. Microsoft announcement.
Google Photos’ free unlimited storage ends June 1. Existing photos will not be removed.
Solar storms will peak in 2025, threatening electronic systems.
The most powerful geomagnetic storm ever recorded resulted in the 1859 Carrington Event, when telegraph lines electrified, zapping operators and setting offices ablaze in North America and Europe. If a storm of that magnitude were to hit today, it would likely cut power to millions of people.
Software Turns ‘Mental Handwriting’ into Onscreen Words, Sentences
Stanford University investigators have coupled artificial intelligence software with a device, called a brain-computer interface, implanted in the brain of a man with full-body paralysis. The software was able to quickly convert the man’s thoughts about handwriting into text on a computer screen.
WarnerMedia is Merging with Discovery
Amazon will acquire the MGM for $8.45 billion
The New York Attorney General released a report on Thursday detailing use of fake comments to influence decisions about network neutrality at the Federal Communications Commission. About 18 million of 22 million submitted comments were fraudulent. The attorney general also announced settlements with three companies involved in the scam totaling $4.4 million in penalties and restitution. Fluent and React2Media were also responsible for millions of fake comments and messages submitted in dozens of other advocacy campaigns.
Security
Ransomware is a growing threat.
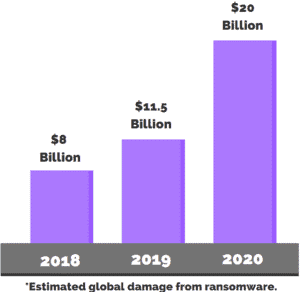
Forbes article: The year 2020 broke all records when it came to data lost in breaches and sheer numbers of cyber-attacks on companies, government, and individuals.
1 in 5 Americans Victim of Ransomware on a personal or work device, and in some cases on both. 46 percent of individuals who experienced an attack on a work device say that their companies went along with criminals’ demands and paid the ransom.
75% of companies infected with ransomware were running up-to-date endpoint protection.
Wall Street Journal: “ … the volume of attacks arrayed against companies means future incidents are inevitable, despite best efforts to address cybersecurity weaknesses.”
Ransomware attack map including Tulare Joint Union High and Selma unified school district.
Colonial Pipeline attack: Everything you need to know.
Ransomware attack on meatpacker JBS likely from Russia.
Recommendations for protection from ransomware
We have had several inquiries from clients since ransomware attacks are making the news.
Here are some basic steps to take to protect yourself.
Prevention:
Maintenance: Fully patched software, adequate malware protection, correctly configured firewall.
Network Security: If you are working from home, treat your home network as part of your business. Make sure any smart home devices have current firmware and adequate passwords. Secure your Wi-Fi. Keep your firewall/router current. Don’t share your work computer/profile with others.
Logins: Use unique, hard to guess passwords. Enable 2 factor authentication for your email, financial websites, and other sensitive logins. Remember that many passwords have been leaked and are being actively used by hackers.
Common Sense: Only you can protect your computer from clicking on something and allowing software to install.
Recovery: The only sure protection is a full backup which is fully isolated from your computers and network. Offsite backups meet this need. Make sure it backs up any databases as well as files.
Experian API Exposed Credit Scores of Most Americans
Experian just fixed a weakness with a partner website that let anyone look up the credit score of tens of millions of Americans just by supplying their name and mailing address.
It is now free in every U.S. state to freeze and unfreeze your credit file.
To file a freeze, consumers must contact each of the three major credit bureaus online, by phone or by mail. Online: Equifax Freeze Page Experian TransUnion
Attackers leveraged trust in Constant Contact email marketing by finding a weakly protected account at USAID to launch an email campaign.
… “don’t underestimate the impact any misuse of your third-party accounts can have to your organization.” … “Treat them like you treat your own infrastructure.”
Your Amazon devices may automatically share your Wi-Fi with neighbors.
Starting June 8th, Sidewalk is a new feature enabling Amazon devices to link together regardless of ownership to access the internet.
Sidewalk-enabled devices use low-energy Bluetooth radios to send their signals up to 100 meters or so. The spherical, fourth-gen Amazon Echo, the Echo Show 10, the Ring Floodlight Cam and the wired version of the Ring Spotlight Cam also use a 900MHz LoRa radio capable of sending and receiving signals from even farther away, with range of up to a half mile.
How Sidewalk can be turned off: Amazon explains
FragAttacks (fragmentation and aggregation attacks) is a collection of new security vulnerabilities that affect Wi-Fi devices.
…many smart home and internet-of-things devices are rarely updated, and Wi-Fi security is the last line of defense that prevents someone from attacking these devices. Unfortunately, due to the discovered vulnerabilities, this last line of defense can now be bypassed.
2021 Verizon Data Breach Investigations Report
Google is going to start automatically enrolling users in two-step verification
Microsoft: 99.9% of compromised accounts did not use multi-factor authentication
99% of all password spraying attacks and 97% of password replay attacks are carried out via legacy authentication protocols.
Humor


By Tim Torian